Crypto Primer
Crypto Example Project
The attached demo project will provide an example implementation of the EC_v1 encryption.
Click this link to download the zip file.
Summary
Encryption Workflow Summary Sensitive data sent in any API call will be field-level encrypted using Elliptic Curve Diffie-Hellman (id-ecDH 1.3.132.1.12). A standard P-256 curve will be used.
UTF-8 encoded bytes of the plaintext JSON "data" dictionary shall be encrypted and included as a Base64 encoded string in the actual JSON payload sent. Field level encryption shall use AES–256 (id-aes256-GCM), with an initialization vector (IV) of 16 null bytes and no associated authentication data (AAD).
Cipher Parms To Get Instance
AES/GCM/NoPadding
Encryptioan Version "EC_v1" Key Derivation Function
Use the key derivation function (KDF) described in NIST SP 800-56A, section 5.8.1, with the following input values:
| Input Name | Value |
|---|---|
| Hash Function | SHA-256 |
| Z | The shared secret calculated above using ECDH |
| Algorithm Id | The byte (0x0D) followed by the ASCII string "id-aes256-GCM". The first byte of this value is an unsigned integer that indicates the string’s length in bytes; the remaining bytes are a variable-length string. |
| Party U Info | The ASCII string "YourProgramCodeHere". This value is a fixed-length string |
| Party V Info | The SHA-256 hash of the UTF-8 encoded bytes of the X-GD-Request-Id value |
| Supplemental Public and Private Info | Unused |
Extract the embedded CryptoV2.zip file and import it into a workspace. Maven can be used to retrieve dependencies. It is incumbent on the developer to update the project with required jar files until the project compiles in their environment.
The two projects in this project can be run after the Maven Update completes.
com.greendotcorp.sandbox.crypto.App.java
Sample application demonstrating encrypt to self, instead of for Green Dot, and decrypt operations using same key pair to provide reference for handling decrypt which needs to also handle parsing of ephemeral public key.
com.greendotcorp.sandbox.crypto.EncryptDataForApiSubmit.java
Working implementation to encrypt data targeting our sandbox public key, which is also included in the project. Again, upon execution, you will see console output.
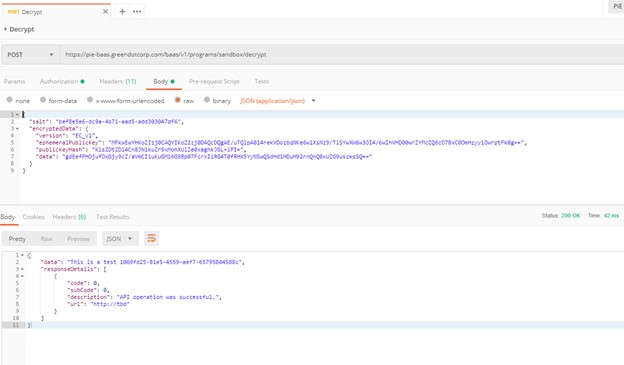
After the encryption code has been run, a JSON payload is produced to the console tab, which can be posted over to PIE with a valid auth token from using sandbox credential to confirm able to decrypt.
Updated 6 months ago
